Domain Logon Failure Event Id

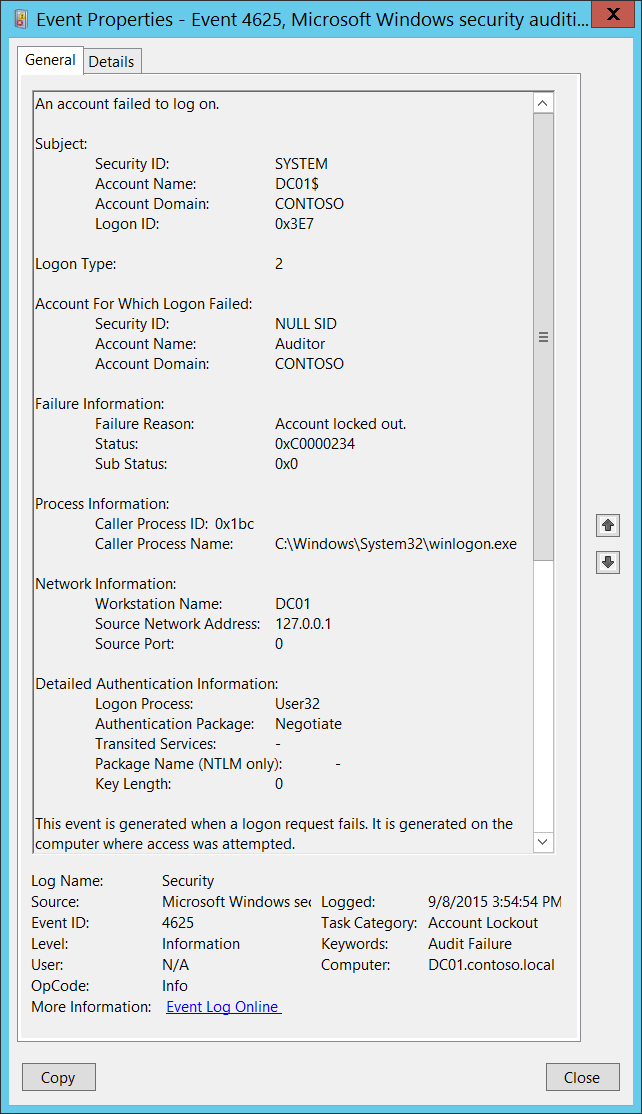
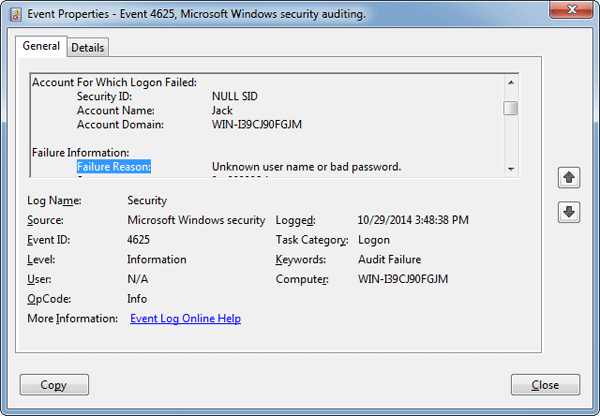
Account for which logon failed.
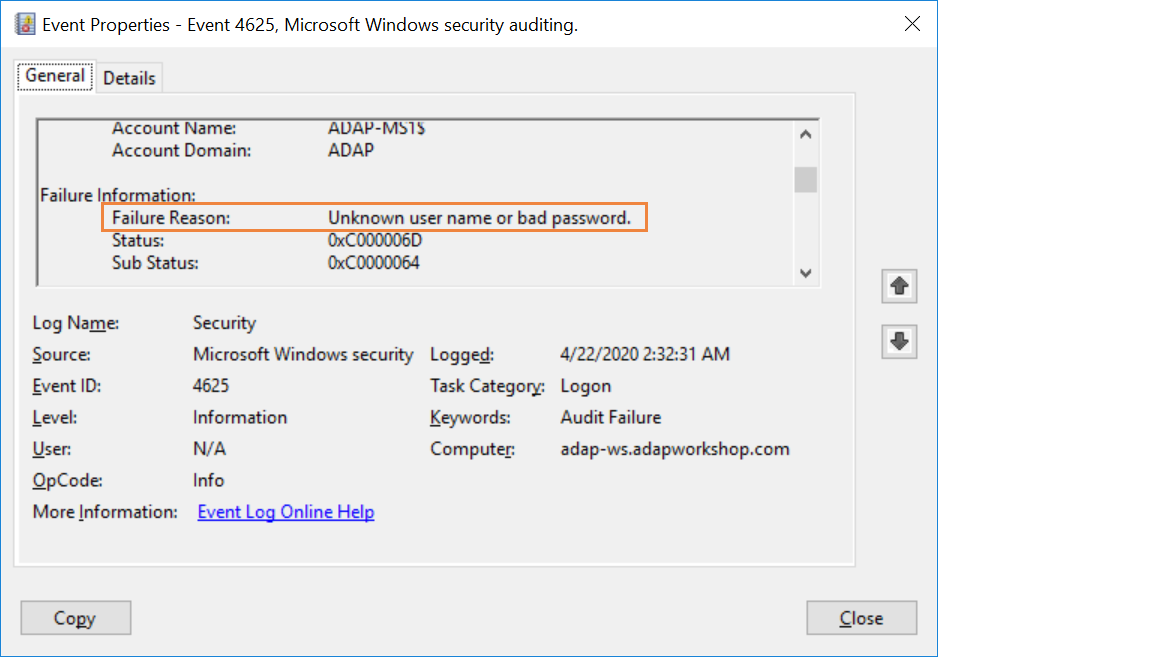
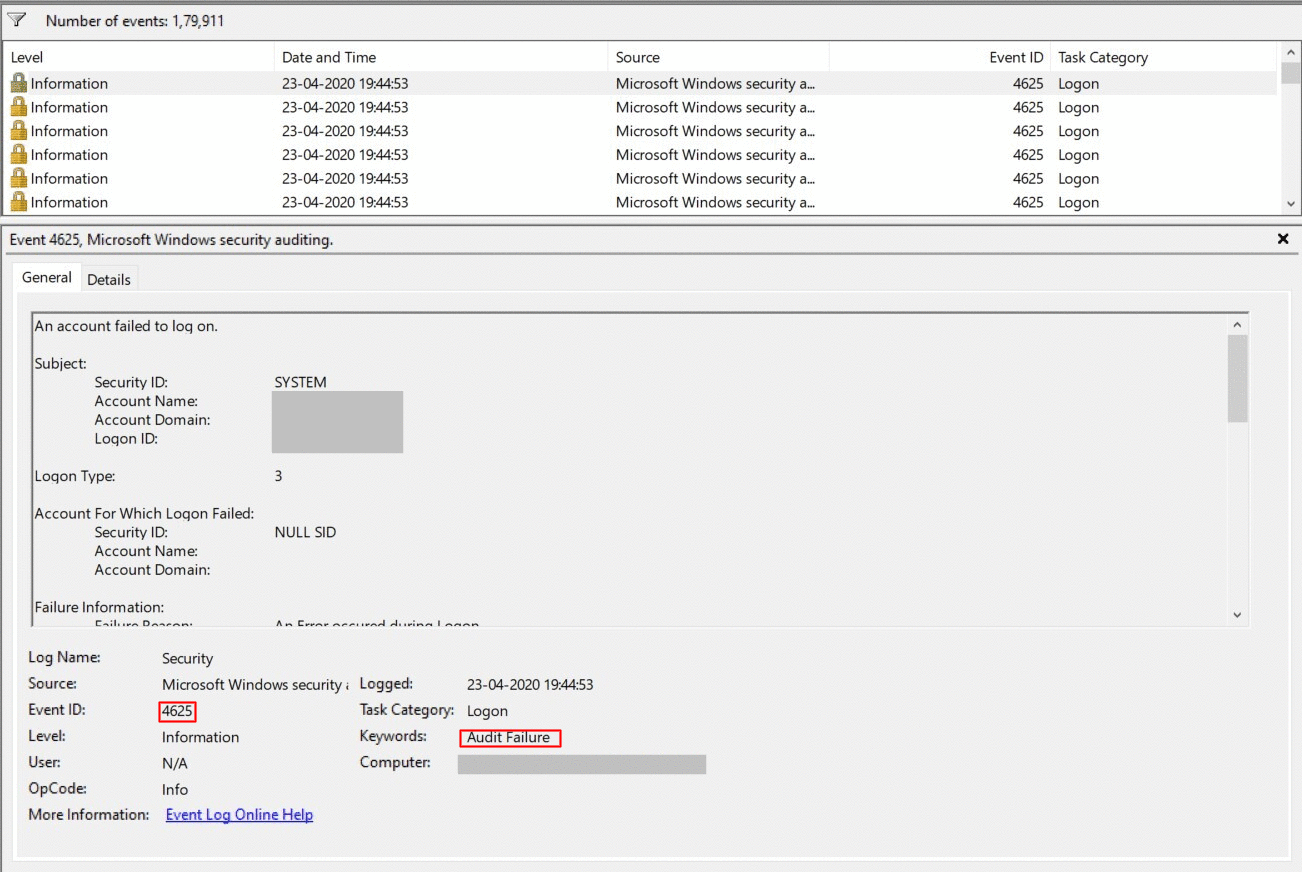
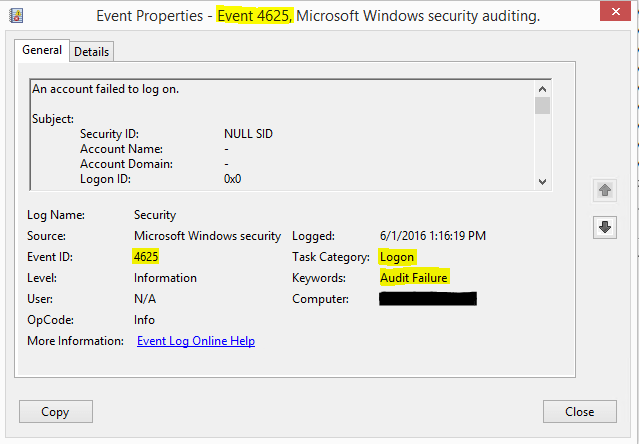
Domain logon failure event id. A related event event id 4625 documents failed logon attempts. Security id type sid. A logon attempt was made with an unknown user name or a known user name with a bad password. This event is generated on the computer that was accessed in other words where the logon session was created.
That means event id 4776 is recorded on the dc. Authentication failure event id 4776 f if the authenticating computer fails to validate the credentials the same event id 4776 is logged but with the result code field not equal to 0x0. A user initiated the. Failed event id 4776 instances on a workstation or member server indicate that some user service or scheduled task attempted but failed to log on by using a local account.
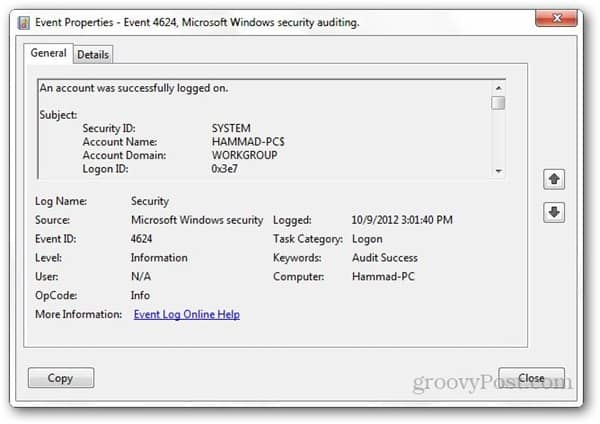
The logoff process was completed for a user. A user successfully logged on to a computer. Event 4624 applies to the following operating systems. See 4624 for a table of logon type codes.
Sid of the account that was specified in the logon attempt. For a description of the different logon types see event id 4624. Any logon type other than 5 which denotes a service startup is a red flag. Let s look at how a user s actions relate to kerberos events.
This section reveals the account name of the user who attempted the logon. Event viewer automatically tries to resolve sids and show the account name. Windows server 2008 r2 and windows 7 windows server 2012 r2 and windows 8 1 and windows server 2016 and windows. Account for which logon failed.
If a local sam account there will be a corresponding failure event from the account logon category. For information about the type of logon see the logon types table below. On workstations and servers this event could be generated by a an attempt to logon with a domain or local sam account. This identifies the user that attempted to logon and failed.
See all result codes in the case of domain account logon attempts the dc validates the credentials. The sid of the account that attempted to logon. Account for which logon failed. You can closely monitor domain logon activity and pinpoint suspicious events.
This is a valuable piece of information as it tells you how the user just logged on. You can determine the.