Domain Trust Sid History

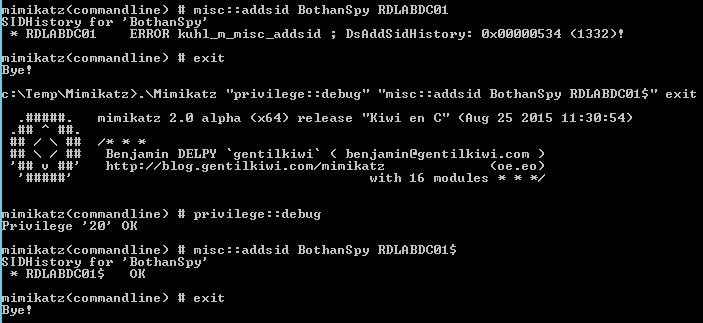
However it is safe to assume that pretty much anyone who can get administrative rights on a domain controller can also add sids to sid history.
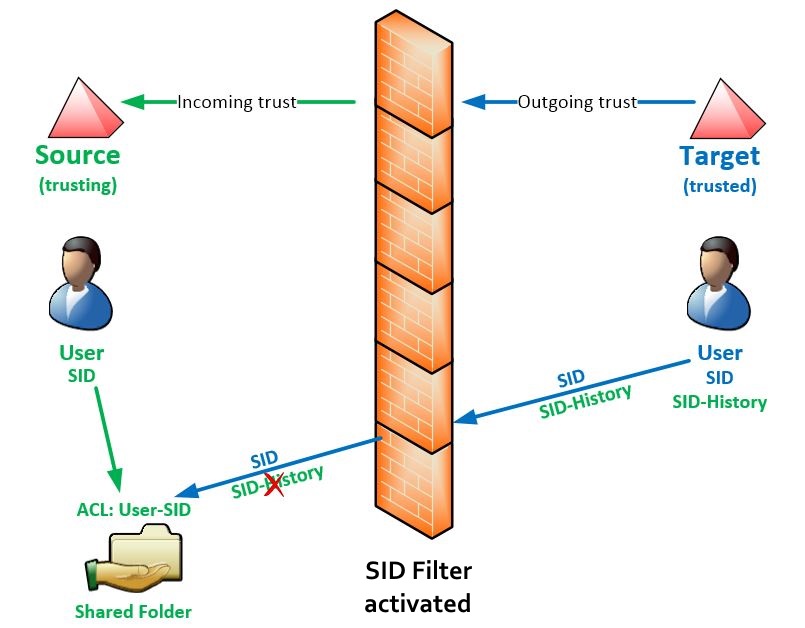
Domain trust sid history. During an active directory migration the sid history is used for migrated user accounts in the trusted domain target to gain access to resources in the trusting domain source. Adding sids to the sid history attribute is a highly privileged function as you can imagine. Since each domain has its own domain sid that object will be assigned a new sid when it s migrated. This is security feature.
Essentially if a user is trying to elevate from a trusted domain the user will add a sid from the trusting domain to that user s sid history. The trust link sees this as a potential compromise and filters from authentication requests all sids that are not from the trusted domain. A regular user in a domain can contain the enterprise admin sid in its sid history from another domain in the active directory forest thus elevating access for the user account to effective domain admin in all domains in the forest. Ideal administration simplifies the administration of your windows workgroups and active directory domains by providing in a single tool all the necessary features to manage domains servers stations and users.
With sid filtering disabled a rogue domain administrator could clone a sid from the other domain and add it to their sid history granting them unauthorized rights. We can enable sid history to allow that object to authenticate against a list of any previous sids assigned to that object. The sid history attribute is what allows this to happen. It performs all the administration tasks like active directory management and reporting remote control operation for windows mac os x and linux active directory file server.
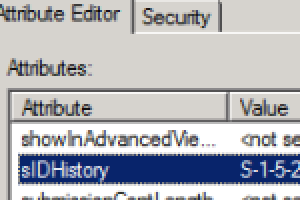
How are sids added to sid history. The sid history of user accounts and groups enables access to resources in the trusting domain in case the filtering is deactivated. Sidhistory can be temporarily enabled until all resources are migrated from the source domain. Depending on whether the existing trust is external or forest based the syntax will.
By default a trust doesn t allows users to access resources by using sid s from their sid history. Disabling sid filtering requires a level of trust between the two forests and ultimately those who are responsible for active directory. Sid history should be enabled on the outgoing trust of the trusting. If you have a forest trust without sid filtering enabled also called quarantine it s possible to inject a sid from another forest and it will be.
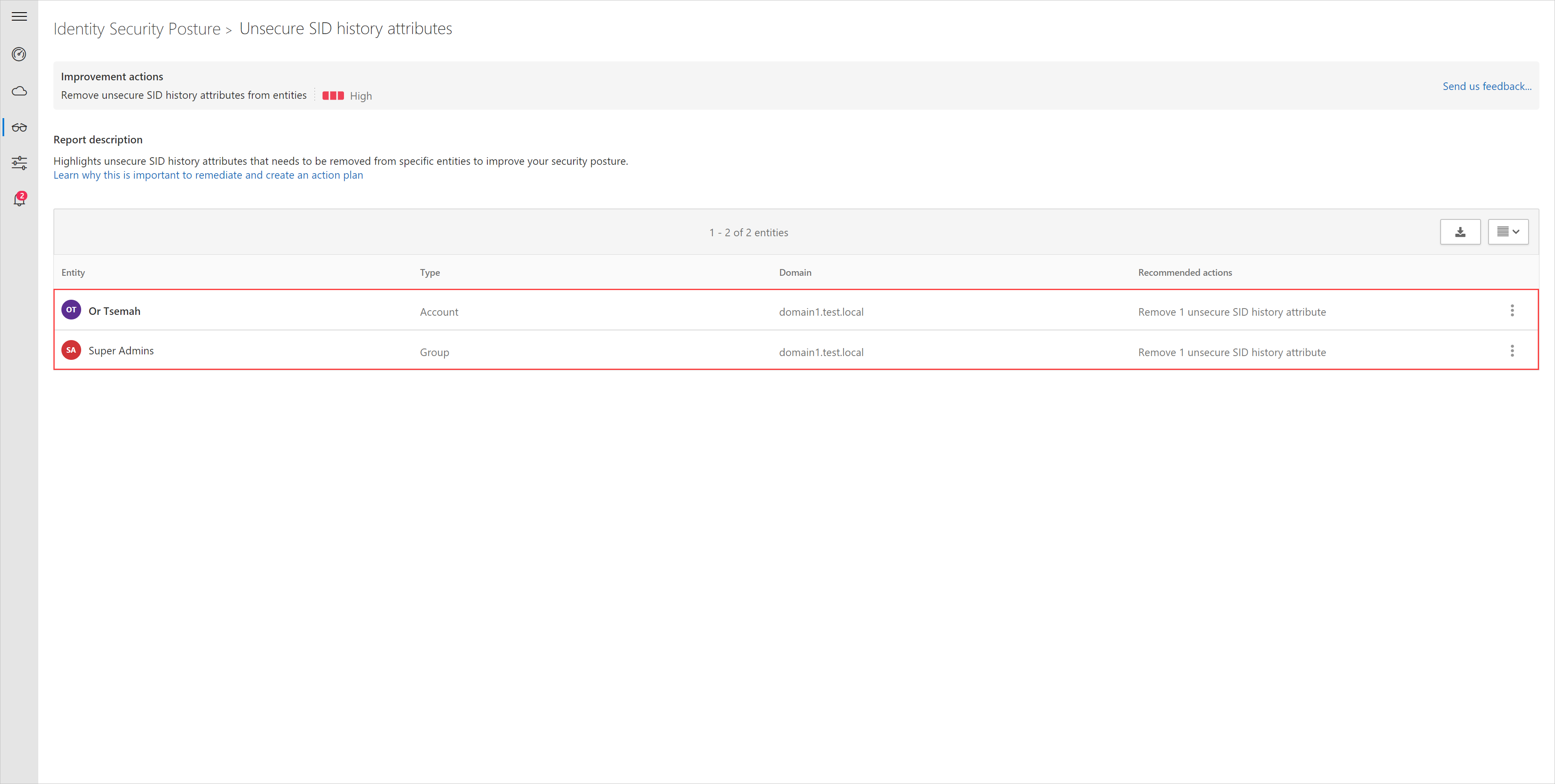
Admt series 1.