Domain Joined Server In Dmz

A small environment might be fine with standalone but beyond a dozen or so servers or with a larger team of staff a separate domain might be easier to manage.
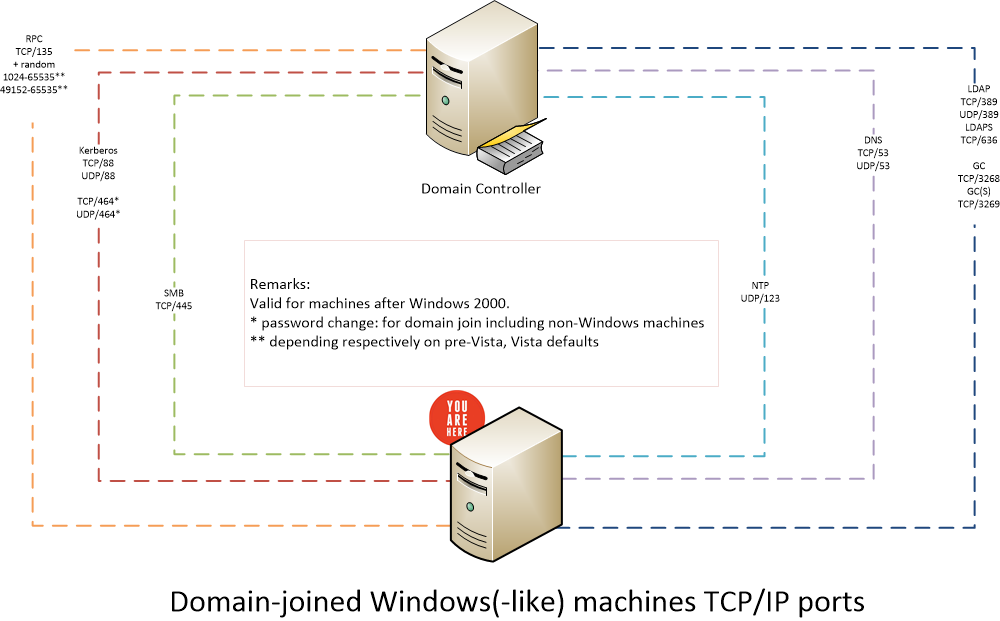
Domain joined server in dmz. I can t join the new server to the domain which is configured with a static 192 168 x x dmz address and i have manually created a dns host record on the dc which has replicated across all dcs and rebooted the server twice. Harden the operating system to only allow authentication traffic access from other servers in the dmz and ad replication traffic from it s ad replication partners in the private network. Block inbound requests from the dmz to the private network should already be done. It is not a good proposal to place domain controllers or extend internal domain within the dmz.
Place the read only domain controller in the dmz. Your dmz servers being joined to your internal domain is a risk that should be avoided. The internal ad domain was by definition extended into the dmz. That said placing a server in a dmz is really only useful if you can actually filter the traffic between it and your internal network.
Not because there was an rodc placed there but because domain member servers were being extended into it. Usually a separated active directory domain for your dmz or running each server standalone is the best option. If it requires domain controller access for authentication database access for back end data and mail access for sending out messages like an exchange cas and you need to open all of those ports between it and internal servers in order for it to actually. Using dmz we are protecting our internal domain from outside world that contains valuable information.